Cyber CLI’s Third Party Risk Management Service
Contact UsThird Party Risk Management (TPRM)
In today’s interconnected world, the security of your business is as strong as the weakest link in your supply chain. That’s why our Third-Party Risk Management service is essential. We help you scrutinize the security practices of your vendors and partners to ensure they meet your high standards. From operational protocols to data handling, we assess every facet of your third parties’ security, giving you the confidence to conduct business safely.
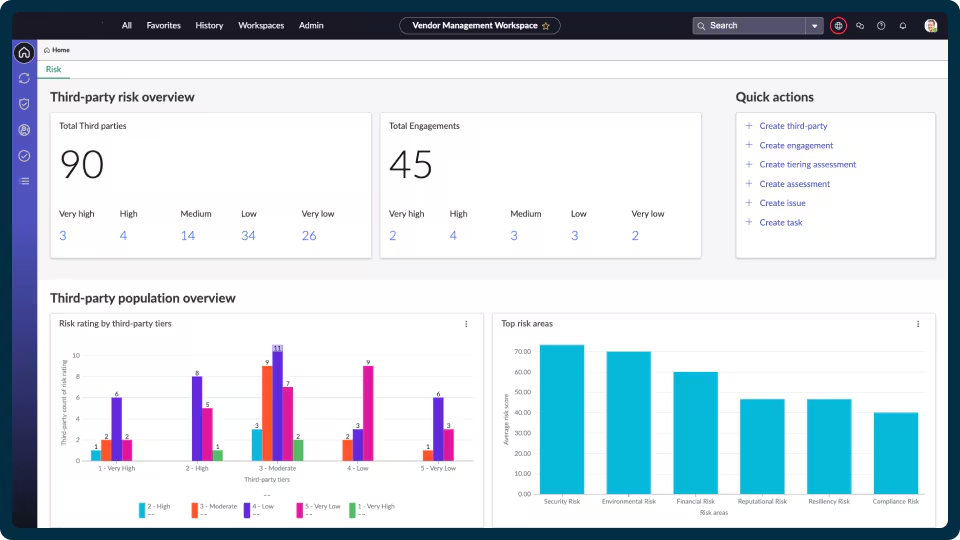
Our Methodology
Our TPRM process is thorough and customized to your unique needs.
Business Logic and Data Flow Understanding
We kick off by diving into your business logic and the data flow between your organization and your third parties, using tools like MS Visio for clarity.
Data Flow Diagram (DFD) Development
A detailed DFD is created to visualize data connectivity, which is crucial for understanding the security controls needed.
Security Checklist Creation
We compile comprehensive checklists to assess your vendors’ security practices, covering operational, system, business continuity, data, and network security.
Assessment and Gap Identification
Through rigorous analysis, we identify any security gaps in your third parties’ practices.
Finalization and Reporting
After a thorough challenge session with the third-party SPOC, we finalize the report detailing our findings and recommendations.
Why Choose Us for Your TPRM Needs
Opting for DefensaNet for your Third-Party Risk Management signifies choosing a partner who places your supply chain security on par with their own. Our methodology is detailed, our assessments are thorough, and our dedication to your organization’s resilience is unwavering.
A focused ally
In identifying and mitigating third-party risks.
Specialized knowledge
In navigating complex compliance landscapes, ensuring your partners adhere to both global and local standards.
An efficient solution
To extend your security perimeter without the overhead of expanding your in-house team.
Access to insights and practices
That are at the forefront of third-party risk management and cybersecurity.
